The Health Insurance Portability and Accountability Act of 1996 (HIPAA) sets guidelines mandating the adoption of Federal privacy protections for health information of individuals which gives patients an array of rights with respect to that information. The HIPAA Privacy Rule ensures federal protections for individually identifiable health information and gives patients a range of rights with respect to that information. The Security Rule defines administrative, physical and technical safety measures to ensure the availability, confidentiality and integrity of electronic protected health information.
Considering that HIPAA is mandatory and since HIPAA violations can impose significant cost to healthcare organizations, third-party tools such as ApexSQL Audit can be helpful in establishing the HIPAA compliance requirements by offering an easy solution to implementing of the HIPAA regulatory requirements related to SQL Server. Implementing the Administrative safeguards, Technical safeguards and Policies and procedures and documentation requirements standards for the 45 CFR Part 164, Subpart C – Security Standards for the Protection of Electronic Protected Health Information that is developed to accomplish protection of electronic protected health information (EPHI)
The following HIPAA Administrative safeguards section requirements regarding SQL Server and supported by ApexSQL Audit with description will be described in the first part of this article:
§ 164.308 (a)(1)(i) – Requires implementing policies and procedures related to SQL Server that will allow detecting, preventing and correcting security violations
§164.308(a)(1)(ii)(D) – Requires that implemented solution allows regular inspection of SQL Server audit logs, access reports and tracking of security incidents
§164.308(a)(3)(ii)(B) – Requires that implemented procedures will ensure tracking whether the access of an employee to EPHI stored in SQL Server is appropriate
§164.308(a)(3)(ii)(C) – Requires that implemented solution will ensure that all SQL Server security procedures that ensures that when an employee leaves organization his access to EPHI, which is defined by paragraph (a)(3)(ii)(B), is terminated
§164.308 (a)(4)(i) – All access to EPHI must be authorized and all authorization policies and procedures must be consistent with the applicable requirements defined in 45 CFR Part 164, Subpart E
§164.308 (a)(4)(ii)(A) – A clearinghouse that is part of a larger organization, must implement policies and procedures to protect access to SQL Servers’ EPHI from the larger organization
ApexSQL Audit
ApexSQL has created the HIPAA compliance checklist for ApexSQL Audit document, with the intention to assist and to show precisely the areas of HIPAA requirements where ApexSQL Audit can help. In the following text the HIPAA requirements that have to be addressed via ApexSQL Audit including how to configure ApexSQL Audit to fulfill that requirement. Recommended SQL Server auditing settings to comply with the individual HIPAA compliance requirements will be described
§ 164.308 (a)(1)(i) Security management process
When implemented as the part of HIPAA compliance solution, ApexSQL Audit will allow easier establishing of security management processes and procedures when HIPAA regulatory is applied to SQL Server. ApexSQL Audit is designed as a tool that can audit all SQL Server related activities including any security related activity and access to any SQL Server object and stores all collected audit data into the single central repository database. All audited data transferred between the audited instance and the central instance are encrypted using SHA256 encryption algorithm. The central repository database is designed as tamper evident which ensure tracking of any malicious change. The audited data archives utilize the tamper-evident design as well, making possible to track unintended or malicious changes of data in archives.
The application utilizes the real-time alerting engine that can be set by user to match any alerting requirement, including the ability for creating the custom alerts based on the user defined T-SQL scripts.
§164.308(a)(1)(ii)(D) Information system activity review
This is the HIPAA requirement that is related to ApexSQL Audit reporting ability in general. ApexSQL Audit is designed to audit and collect any SQL Server related event, which coupled with the comprehensive reporting abilities will ensure displaying all required information according to HIPAA requirements in the consolidated form with ability for full customization of the generated reports according to any special requirements
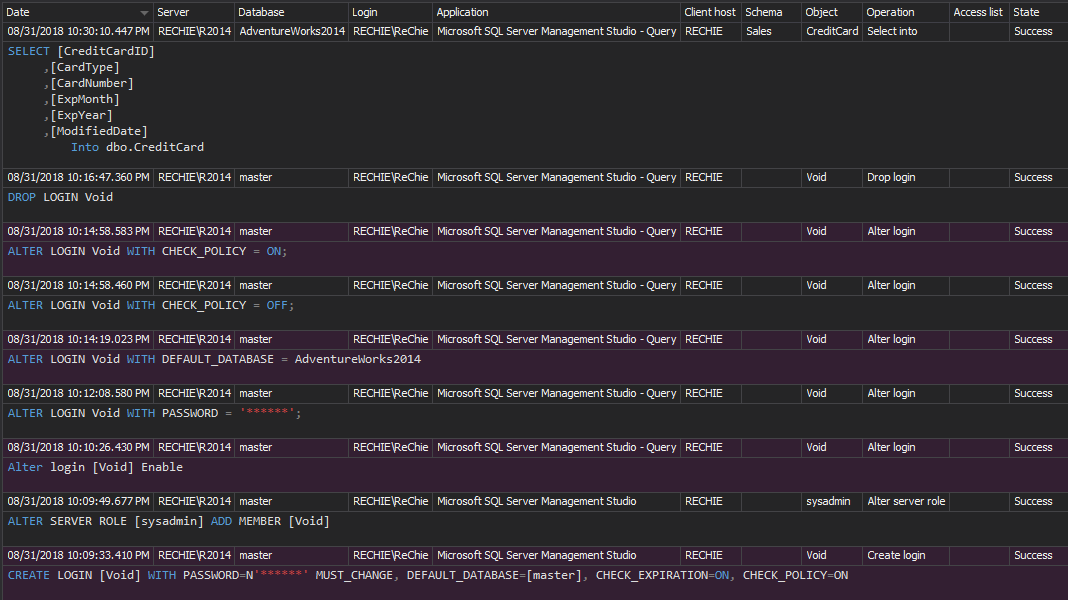
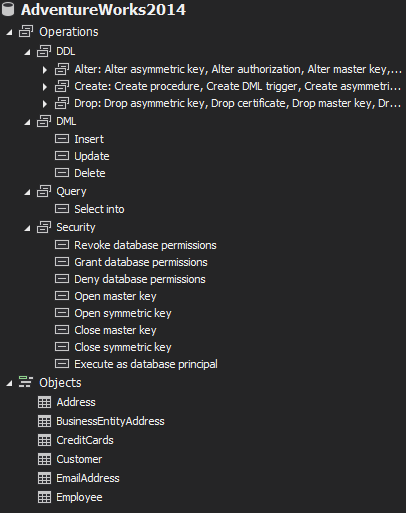
ApexSQL Audit can report on all collected event with all the information needed to allow properly qualifying and identifying of individual events in report and the following image shows the information columns that are available for the collected SQL Server events.
The image below displays all the information columns available for the SQL Server’s events collected by ApexSQL Audit
ApexSQL Audit features two types of reports – common or custom reports, and its design allows matching all HIPAA related requirements including any need for the specific individually designed reports. More details about ApexSQL reporting can be found in the ApexSQL Audit Feature highlight: Custom reports article
§164.308(a)(3)(ii)(B) Workforce clearance procedure, §164.308(a)(3)(ii)(C) Termination procedures, §164.308 (a)(4)(i) Information access management, §164.308(a)(4)(ii)(C) Access establishment and modification
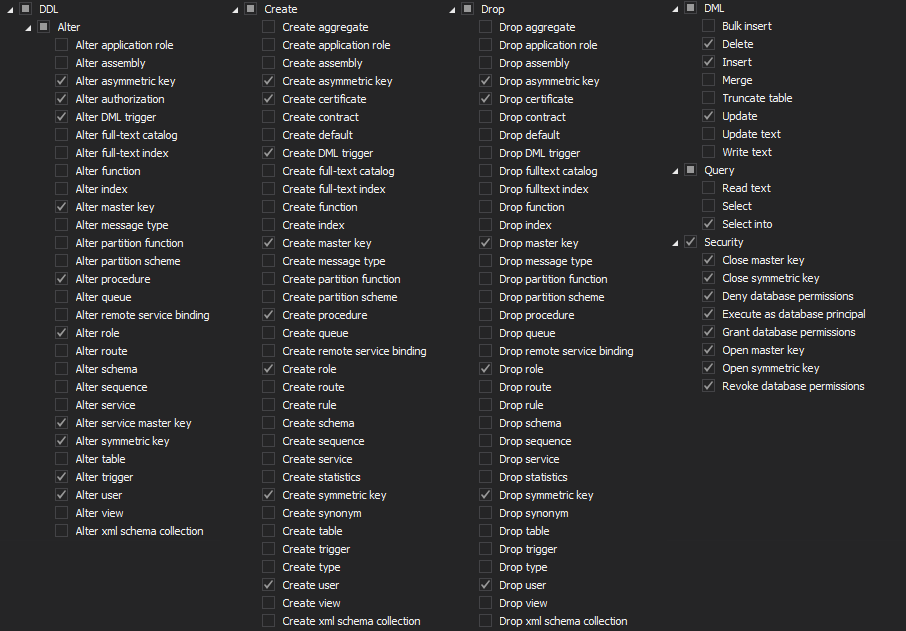
This requirement is focused on ensuring the necessary auditing, appropriate alerting and reporting on all login/user related changes on a server and/or database level including any role/permission changes. This ensures that all login/users have appropriate privileges and access to EPHI that is limited/defined to comply to the HIPAA/internal security rules, whichever is stricter. The best practice is to include setup of the alerts for all or at least for non-trusted login/users changes/access to EPHI data and review of any EPHI change/access using the reporting ability of ApexSQL Audit. Below is the minimum auditing filter configuration that should ensure these HIPAA requirements
NOTE: Steps that will be described in this requirements section are mostly the common steps, self-explainable in general and therefore they will not be addressed every time in describing the rest of the HIPAA requirements in this article, in favor of showing only the specific filtering conditions required for matching that specific HIPAA requirement
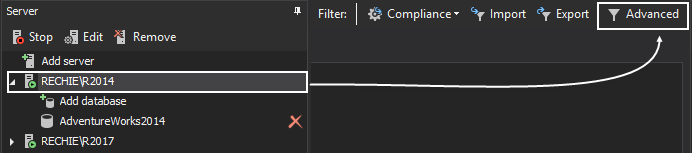
To set the simple auditing filter:
After selecting the SQL Server instance for which activities must be audited, select the proper server and database level set of operations
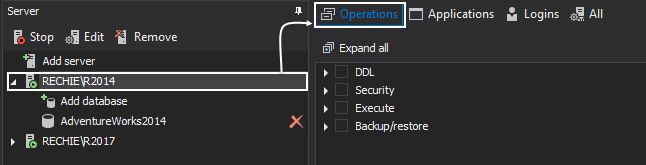
Server level auditing filter should utilize the following filter settings
Select databases that needs to be audited via Add database
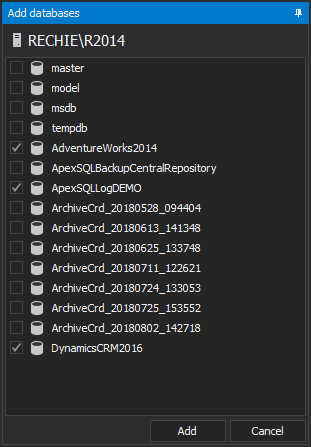
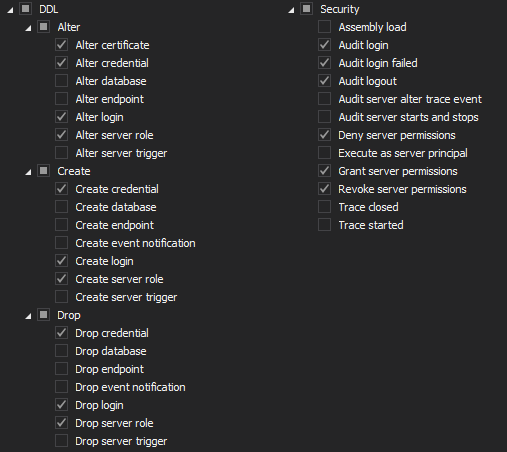
The database level auditing must include the following filter settings
In situation when only particular tables store the EPHI data, ApexSQL Audit Object filter allows auditing of only these tables. The filter allows including only the user specified tables for auditing
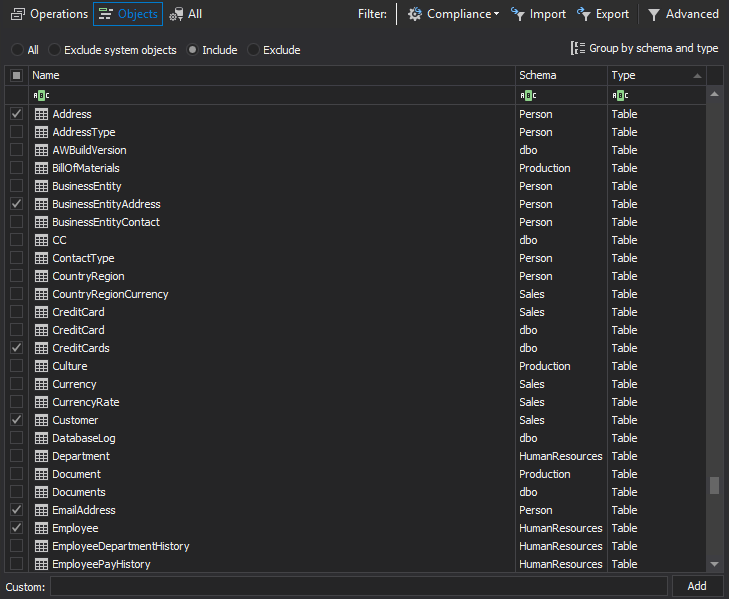
Choose Include radio button inside the Objects filter configuration to load the database tables that contain EPHI data to be added for auditing
Sort the objects by Type to select the Table sets and by tickling the checkboxes tables are added for auditing. Once the filter is set, only the tables listed in the Summary pane (Include objects) will be audited
Repeat the procedure for each database added for auditing, but keep in mind that in case when some auditing requirements are different for different databases, auditing filter configuration has to be defined according to the specified requirements for each database
The advanced filter is logical expressions based, which allows, in many situations, to set up the required filtering condition faster while achieving the equal filtering criteria as with the simple filter or even more precise when required
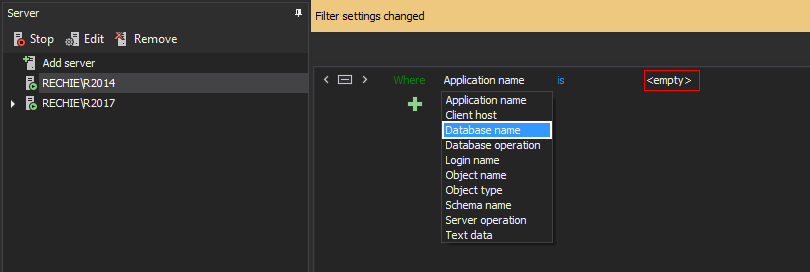
After selecting the Advanced button in the filter configuration pane, click  and the filtering condition will be added. Now click on the data field to expand the drop-down menu with filtering conditions and select Database name
and the filtering condition will be added. Now click on the data field to expand the drop-down menu with filtering conditions and select Database name
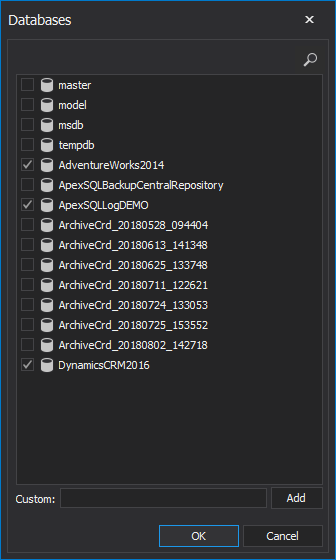
Click on <empty> to open the Database browser and select desired databases to add
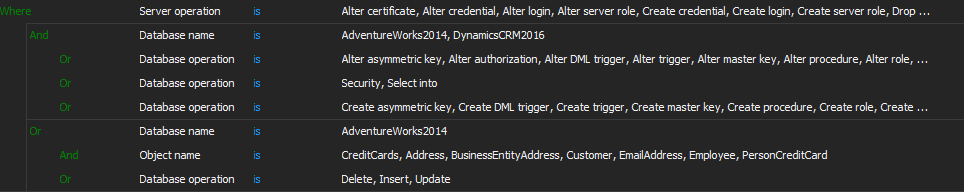
In the same manner add other advanced auditing conditions to get the following advanced filtering condition that matches the above defined simple filter and therefore the HIPAA requirement
In the above Advanced filter example, only the selected AdwentureWorks2014 tables are set for DML auditing. For each database this should be set according to specific internal requirements and/or depending on the way of HIPAA compliance implementation
Regardless of the filter used, setting up the real-time alerting will ensure informing the person in charge on any unexpected change or access to EPHI data. It is recommended creating the alerts for the database tables that contains the EPHI data and alerts that will track any login/user changes.
EPHI data is not prone to change often, so each and every DML change and/or access of unauthorized users is the potential issue and should be verified by authorized person as soon as possible. To set the alerts for tables that contain EPHI data:
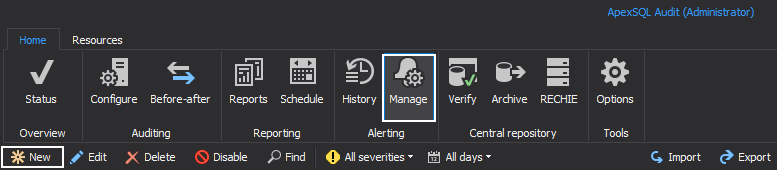
Select the Alerts tab and then in the Manage tab select New
Select Auditing alert
In the New alert wizard, Basic settings dialog provides fully customizable fields for specifying the alert name, subject and report body text. If used, the Limit the number of reports for this alert to one per minute (for each server) option prevents an excessive amount of the alerts in situations when number of events spike. In such cases where the sensitive data are not likely to be change often and taking in account their importance, it is recommended to leave this option unchecked
The next Server deployment dialog requires selecting the SQL Server instance
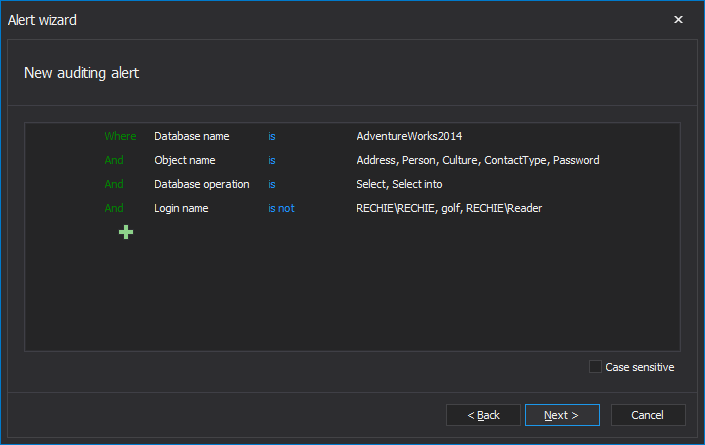
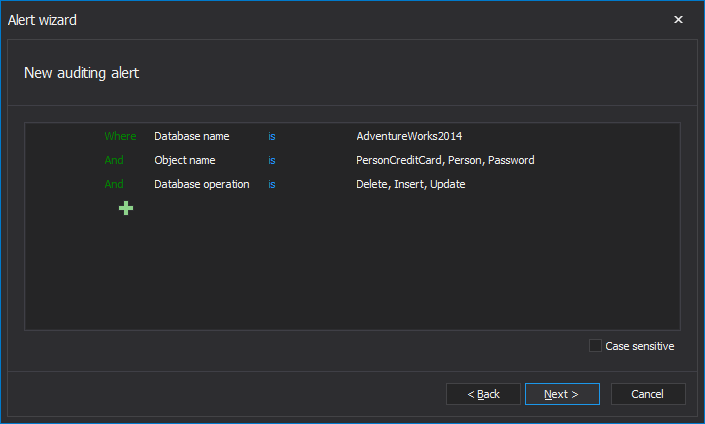
Defining the alert condition is implemented via the advanced filter, and in this particular situation described here the filter example that will raise alerts for SELECT or Select into access on listed tables in particular databases and with defined users that are not permitted to execute that. In the example below, the Rechie\Rechie, golf and Rechie\Reader are excluded from alerting as they are authorized to access the EPHI data
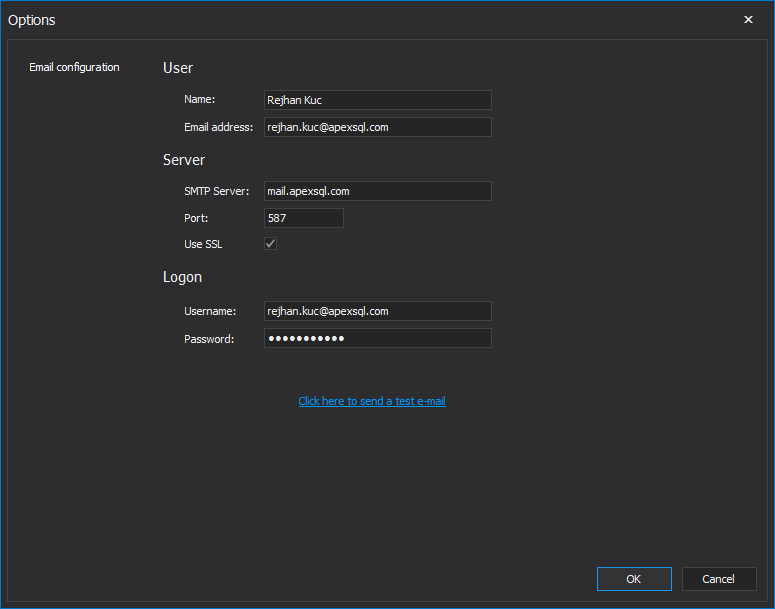
In the next Actions step, select the Send this alert report via email checkbox to get notified via email when alert occurs
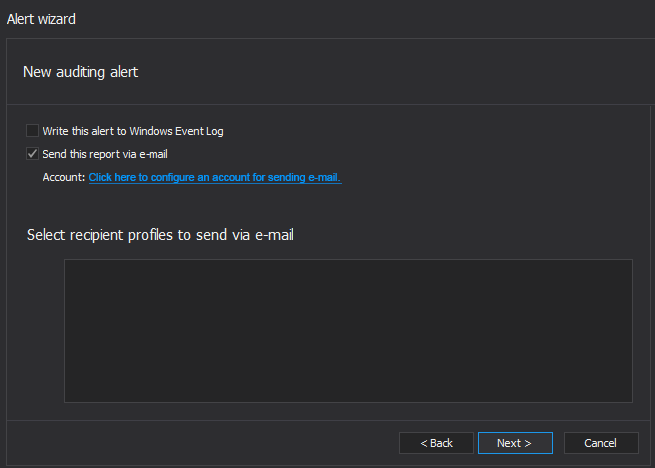
To configure the SMTP email account that will be used for sending email when an alert is triggered, set up the SMTP mail account via selecting the Click here to configure an account for sending e-mail link
At the end, the Alert summary dialog will show all the information about the alert
Besides this, creating the following alerts will help significantly in implementing and complying to the specified requirements in this section. In the following text the required filtering conditions for creating the appropriate alerts will be shown with appropriate examples
Alerting on any login/user change
To track any DML change on the sensitive tables containing EPHI data
By setting up SQL Server auditing and alerting like it was described, ApexSQL Audit will be configured to track and provide detailed information on any unapproved, inadvertent and intentional change of data and thus reducing the threat of violation of SQL Server data. At the same time, real-time alerts can ensure a quick and timely response when any data change events occur
In the Part 2 of this article we will describe the remaining supported HIPAA Administrative safeguards, along with supported Technical safeguards and Policies and procedures and documentation requirements sections requirements
Related Posts:
- SQL Server auditing and compliance for FERPA
- PCI Compliance for SQL Server DBAs
- How to implement HIPAA regulatory standard for SQL Server – Part 2
- How to implement compliance with the PCI DSS regulatory standard for SQL Server – Part 3
- SQL Server compliance requirements
August 31, 2018
August 31, 2015