Health Insurance Portability and Accountability Act (HIPAA) is a security act that sets standards for ensuring security, privacy, confidentiality, integrity, and availability of patient health information – electronic Protected Health Information (PHI).
The HIPAA compliance requires access control, information integrity, audit control, user authentication and transmission security. Similarly as with other compliance regulations, it’s necessary to use software, hardware, or other methods that provide monitoring and capturing of user activities in information systems that contain or use electronic PHI. The security and integrity of electronic PHI must be ensured against any unauthorized access, modification, and deletion.
“As required by Congress in HIPAA, the Privacy Rule covers:
- Health plans
- Health care clearinghouses
- Health care providers who conduct certain financial and administrative transactions electronically. These electronic transactions are those for which standards have been adopted by the Secretary under HIPAA, such as electronic billing and fund transfers” [1]
To be able to meet the HIPAA requirements, the entity must constantly audit and report all access attempts and events related the databases and objects that contain sensitive PHI records.
Depending on the structure of health institution entities, supervisors periodically perform verification of HIPAA compliance to ensure its effectiveness. The verification frequency depends on the last verification report, and it’s less frequent in case of previous or constant positive HIPAA compliance.
The HIPAA act requirements do not strictly address methods for database and IT security. However, according to the regulation requirements on providing integrity, confidentiality, privacy, and availability of patient health information, the following steps provide compliance with HIPAA:
- Define and document the required permissions for each health institution employee
- Periodically review permission configurations on database objects and modify access rights in order to maintain the integrity, confidentiality, and accuracy of the PHI records
- Audit the system that keeps and provides use of the PHI records
- Analyze the audit information that show events related to the PHI records periodically, and take action where needed
HIPAA compliance – general recommendations for SQL Server DBAs
The following general actions are recommended in order to comply with HIPAA regulations:
-
SQL Server environment that’s secure and controlled constantly. Provide SQL Server system security with continuous auditing of system events, whether the events are internal or external. Ensure this by enforcing strict rules unchangeable by unauthorized parties. Apply the rules to all SQL Server objects related to confidential PHI data (logins, databases, users, tables, etc.)
After the rules are set, audit and periodically analyze all events related to security – particularly pay attention to permission changes on the SQL Server objects, and access to databases/tables with PHI records
- Whatever the user origin is (internal or external), his/her actions must be monitored and documented in appropriate audit reports when related to database/table access permission changes. Administrative personnel actions must be documented as well – there must be no difference between regular users and administrators when it comes to auditing
-
Use secure and officially verified hardware and software. Pay attention to common security configuration omissions, like default logins and passwords, that are often used by intruders in attack attempts
Modify all default system supplied security parameters on SQL Server. If possible, do not use the mixed mode (enables both Windows and SQL Server authentication), switch to the Windows authentication only. When used for accessing SQL Server, the Windows authentication ensures the Windows password policy – checking the password history, and the password length and life duration. The most important feature of the Windows password policy is the login lockout – it gets locked for further use after a number of consecutive failed logon attempts.
- Any changes or tampering of captured audit information must be evident, whether it was done by an external or internal party. Tampering attempts monitoring is required in terms of compliance regulations, intrusion preventions, and potential security breach investigations
HIPAA compliance recommendations for SQL Server auditing
In order to comply with HIPAA regulations, it’s required to audit, document and provide reports for all security related events on the SQL Server instance that stores PHI records and its objects.
During the HIPAA compliance revision, the reports that show security changes on SQL Server access and activity are required, although the regulations are not strict about the report details.
ApexSQL Audit is a SQL Server auditing and compliance tool that tracks and reports all security related events on SQL Server by auditing access and changes to the instance and its objects, and ensures compliance with HIPAA regulations. It provides a range of built-in reports which are commonly requested by an audit revision personnel to ensure the compliance regulative adherence.
ApexSQL Audit helps in the process of meeting HIPAA regulations as it:
- Automatically monitors and records security events and user actions that can potentially jeopardize safety, accuracy, and privacy of PHI data
- Identifies risks on compliance and SQL Server security vulnerabilities
- Offers tamper evident, accurate, and comprehensive reports for compliance reviews
The following HIPPA standards and implementation specifications are related to the SQL Server auditing process, and supported by appropriate ApexSQL Audit reports:
HIPAA Standard 164.308(a)(1) – Security management process
“Implement policies and procedures to prevent, detect, contain and correct security violations.”[1]
Changes on the auditing configuration must be monitored and reported. It’s important to indicate lapses made on the auditing configuration and correct them on time. Reports about auditing configuration changes are essential in providing help with that.
-
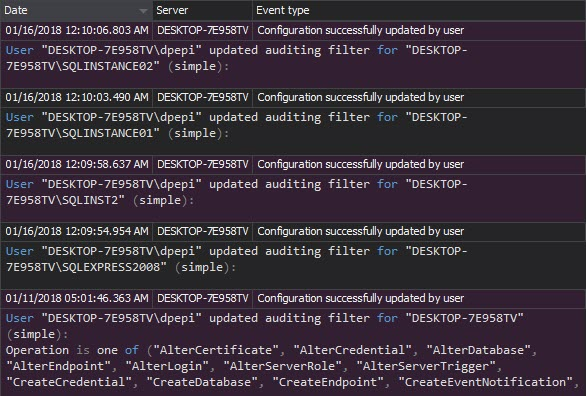
The Audit settings history report shows all changes made to the ApexSQL Audit auditing configuration. Once set, the auditing configuration must be audited for changes as any other security related entity change can be indicative and should be investigated
-
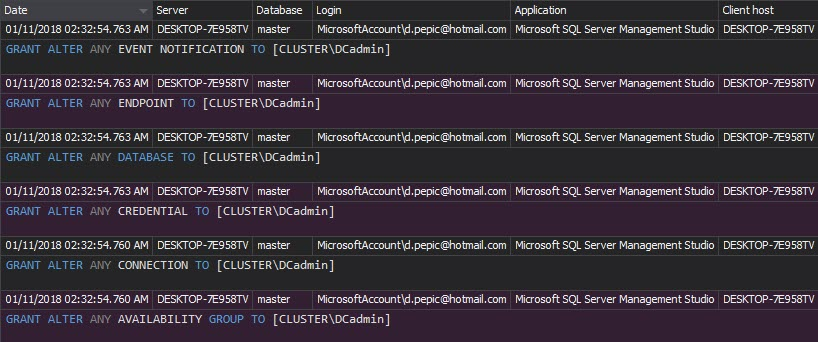
The Security configuration history report provides all changes on the SQL Server logins, users, and roles. The report shows username and password changes, created/dropped entities, and changes on permissions. Each report entry is to be considered as a potential threat and alert
HIPAA standard 164.308(a)(1)(ii)(D) – Information system activity review
“Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports.” [1]
Auditing access to the confidential PHI information is a must to meet HIPAA requirements – any access should be reported, legitimate or not. The following ApexSQL Audit reports provide access information:
- The Complete audit trail report provides all captured events on the audited SQL Server instance. The report shows a history of events and can help in finding suspicious event patterns, e.g. successful logons followed by denied access or secured data warnings
-
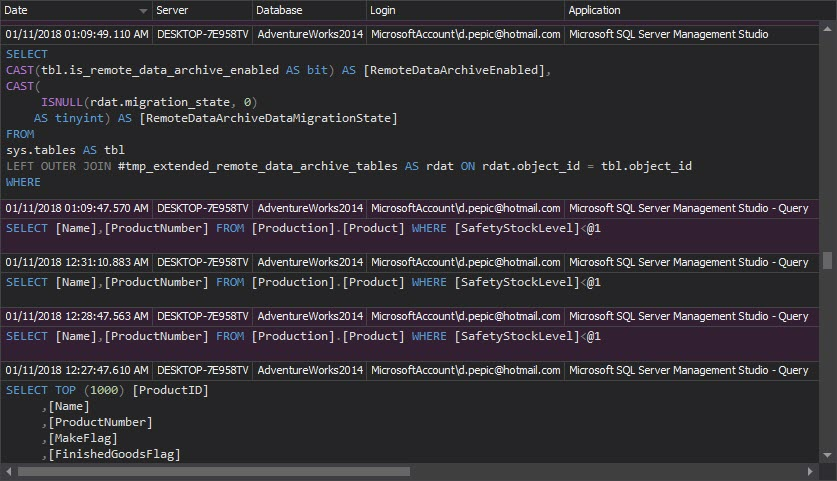
The Access history report shows all access events on objects in SQL Server. It provides executed T-SQL statements and stored procedures used to access audited objects
Tracking user logons to the system is important for any compliance regulation – any logon attempt must be documented, successful or not
-
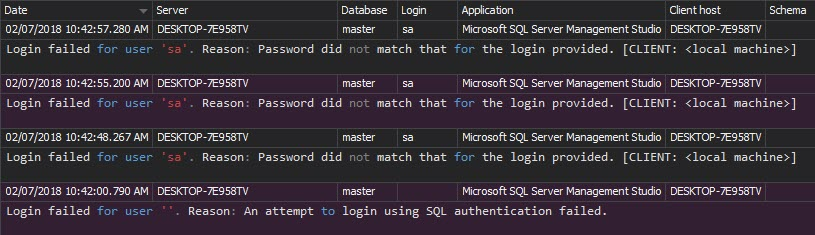
The Unauthorized access report can indicate attack attempts and provide information on attacker targets (e.g. certain logins on SQL Server instances). All unsuccessful logons, caused by wrong passwords or non-existing logins are shown in the report
HIPAA Standard 164.308(a)(3) – Workforce security
“Implement procedures for the authorization and/or supervision of workforce members who work with electronic protected health information or in locations where it might be accessed.” [1]
- The Access history report shows all access events on objects in SQL Server. They provide executed T-SQL statements and stored procedures used to access audited objects
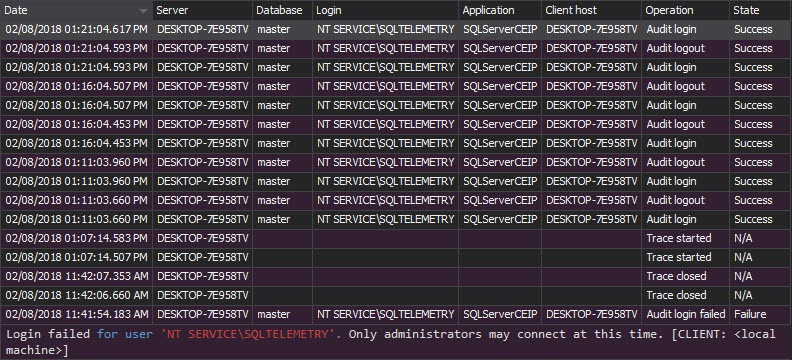
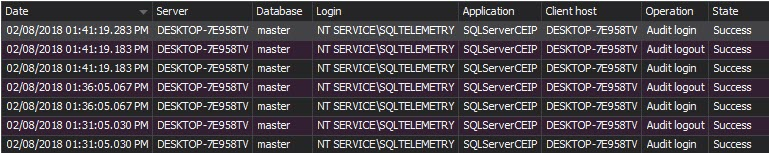
- The Logon activity history report provides history of user authentication. For each logon attempt, the application, application host name, SQL Server instance, login, time, and logon status are reported
HIPAA standard 164.308(a)(4) – Information access management
The Information Access Management includes the following two implementation specifications:
-
Access Authorization 164.308(a)(4)(ii)(B)
“Implement policies and procedures for granting access to electronic protected health information; for example, through access to a workstation, transaction, program, process, or other mechanism.” [1]Once the strict permissions for system users are set, use the previously described Security configuration history report to make sure no unapproved changes are made and the initial permissions are in place. The report shows username and password changes, created/dropped entity, and changes on permissions
-
Access Establishment and Modification 164.308(a)(4)(ii)(C)
“Implement policies and procedures that, based upon the entity’s access authorization policies, establish, document, review, and modify a user’s right of access to a workstation, transaction, program, or process.” [1]Any action that changes security settings must be reported in order to comply with HIPAA. Such actions can be a potential threat to data integrity and safety
HIPAA standard 164.308(a)(5)(ii)(C) – Log-in monitoring
“Implement procedures for monitoring log-in attempts and reporting discrepancies.” [1]
-
The Logon activity history report provides the history of all logon attempts, both successful and unsuccessful. For each logon attempt, the application, application host name, SQL Server instance, login, time, and logon status are reported
Complying with HIPAA regulations requires a SQL Server DBA to set up and configure environment with secured conditions for the confidentiality and integrity of the PHI records. With comprehensive historical reports and a range of fine-tuning auditing options, ApexSQL Audit provides auditing of Server instances, and helps meeting the HIPAA compliance requirements at the same time
References:
[1] About the Privacy Rule FAQs
Useful resources
HIPAA Administrative Simplification
Health Information Privacy
Health Insurance Portability and Accountability Act
HIPAA Regulations
HIPAA privacy and security toolkit – American Medical Association
The HIPAA Law and Related Information
January 16, 2014