What is SOX
The Sarbanes–Oxley Act of 2002, Sarbanes–Oxley, Sarbox, or SOX is a regulation created to improve the quality and integrity of financial reporting. It addresses audits, financial reporting and disclosure, conflicts of interest, and corporate governance, so financial and business information is factual and accurate. Its purpose is to avoid accounting scandals like the ones in 1990s stock market.
Who has to comply with SOX?
All US public companies, management, and public accounting firms have to comply with SOX.
What is SOX meant to ensure?
SOX introduces strict procedures and requirements for financial reporting. These procedures ensure reliability of publicly reported financial information, as the reports are created according to Generally Accepted Accounting Principles (GAAP) and thus represent the true information and financial state of the company. This prevents potential corporate frauds, undue risks, protects company assets and creates a sound financial environment.
How is SOX compliance verified?
Top management of the company must individually certify the accuracy of corporate financial information. The annual reports are then submitted to independent, external auditors who review the report accuracy. The independent auditors also attest the internal controls for financial reporting, so the company must ensure that adequate controls, including IT, are set and constantly enforced.
How does SOX affect IT?
Unlike HIPAA and PCI regulations, SOX is not very specific and straightforward when it comes to regulations that address IT. The only section that addresses IT control practices is 404:
“SEC. 404. MANAGEMENT ASSESSMENT OF INTERNAL CONTROLS.
- RULES REQUIRED.—The Commission shall prescribe rules requiring each annual report required by section 13(a) or 15(d) of the Securities Exchange Act of 1934 (15 U.S.C. 78m or 78o(d)) to contain an internal control report, which shall –
- state the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting; and
- contain an assessment, as of the end of the most recent fiscal year of the issuer, of the effectiveness of the internal control structure and procedures of the issuer for financial reporting.
- INTERNAL CONTROL EVALUATION AND REPORTING.—With respect to the internal control assessment required by subsection (a), each registered public accounting firm that prepares or issues the audit report for the issuer shall attest to, and report on, the assessment made by the management of the issuer. An attestation made under this subsection shall be made in accordance with standards for attestation engagements issued or adopted by the Board. Any such attestation shall not be the subject of a separate engagement.”1
It doesn’t mention network protection, user accounts, access control, data encryption, or monitoring. Although the Section 404 doesn’t clearly state what should be done on a database that stores company accounting data, it represents the request for providing accurate and factual business and financial reports. To guarantee that the reports are based on true data, it’s necessary to verify that the records protected from tampering and modification by an unauthorized person.
To protect data accuracy and integrity, it’s recommended to identify the minimal permissions on data for each employee and deny any privileges above minimal. Once the permissions are set, monitor permission changes to make sure the security rules are enforced. It’s also recommended to audit all activity on all SQL Server instances and databases that contain financial reporting and accounting data.
This is where ApexSQL Audit can help, as it:
- Automatically monitors events on SQL Server instances and databases to make sure sensitive data is protected for unauthorized access and changes
- Provides accurate and relevant reports for internal control evaluation and reporting, and external auditors
- Provides reports that discover threats and security incidents
Tracks any potential audit tampering
How to audit a SQL Server instance
ApexSQL Audit is a SQL Server auditing tool that provides a variety of options for auditing SQL Server events, ensures compliance with policies, and monitors SQL Server security by tracking permission, login and password changes. It has a range of built-in reports, commonly needed for compliance auditing. For more specific requests, custom reports can be created using a drag-and-drop technique.
The ApexSQL Audit reports that help with SOX compliance
Audit reports should be created regularly in order to confirm company internal controls are enforced, or diagnose any discrepancy which could lead to failing to comply with SOX.
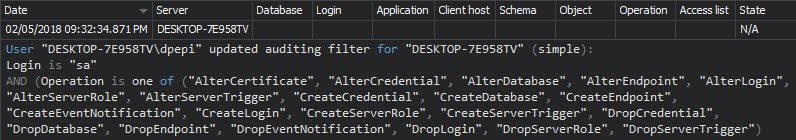
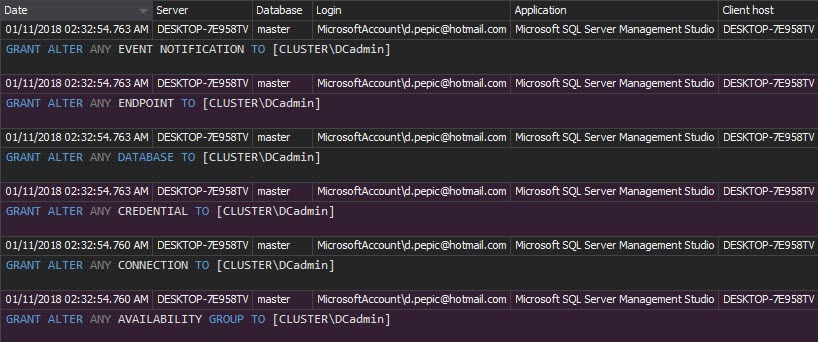
Once auditing is set properly, it shouldn’t be changed, unless documented. The Audit settings history report shows the auditing setting changes. Unexpected changes should be investigated, as they can lead to incomplete audit trails, and thus threaten data security:
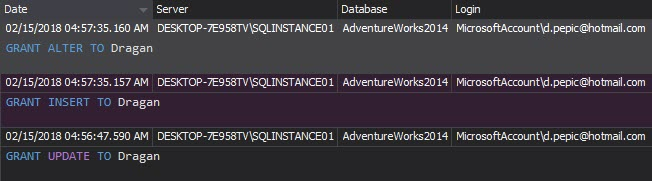
Once the security rules are set, it’s necessary to monitor all changes to permissions and security settings and investigate any undocumented change. The Security configuration history report shows changes on logins, users, and roles:
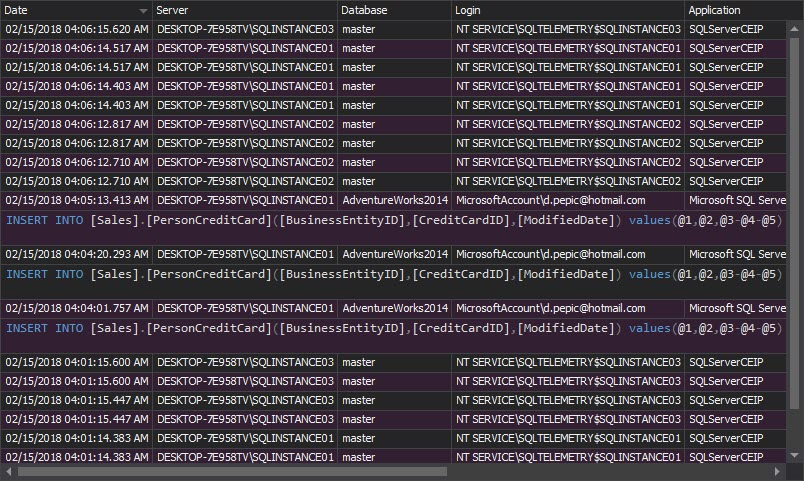
The Complete audit trail report shows all events that happened on all audited SQL Server instances:
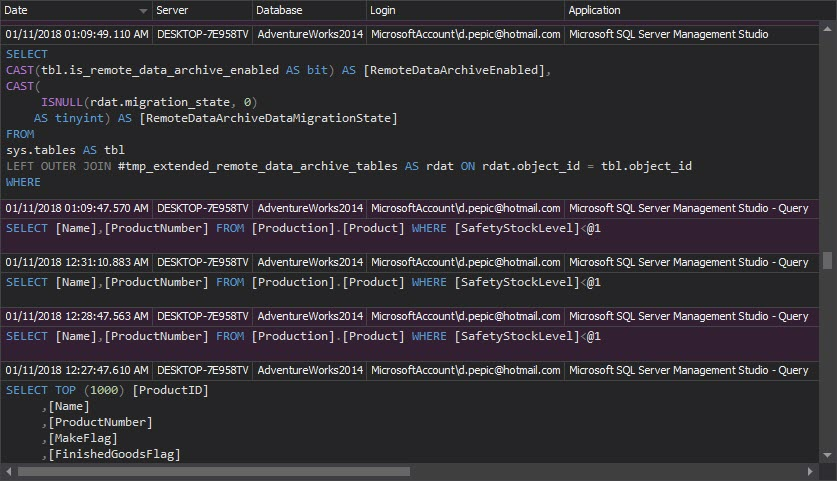
The Access history report shows who accessed what, when and what changes were made:
The Permission changes report shows who, when and how changed the user’s permissions and the permissions granted/denied to SQL Server roles and role membership changes – logins added or removed. This report help tracking whether the users have been granted more than minimal privileges. Any unexpected and unapproved permission changes must be investigated:
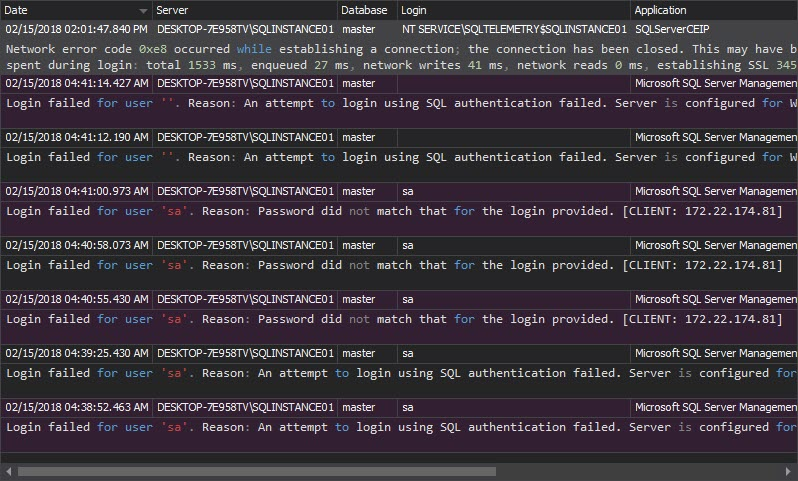
The Unauthorized access report shows failed login attempts, when non-existing logins or wrong passwords are used:
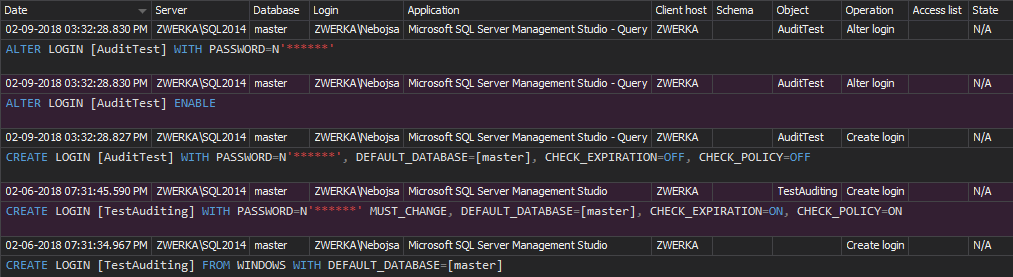
The DDL history report shows the users created/deleted on a database, who and when created/deleted them:
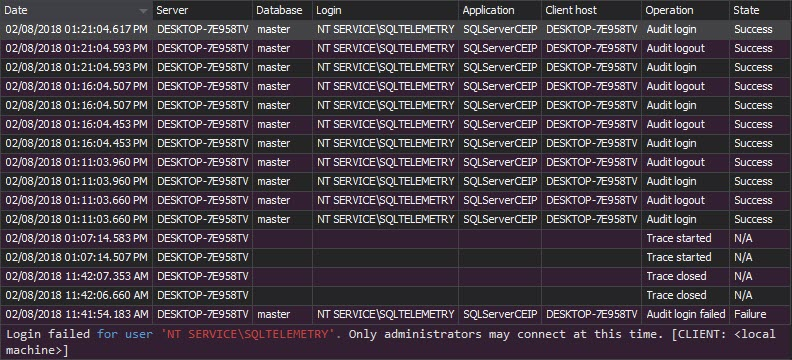
The Logon activity history report shows who and when has attempted to logon to the SQL Server instance along with the time, logon attempt status and machine name:
Although SOX compliance regulations don’t specifically address IT departments, it’s clear that financial reporting and accounting data integrity can be achieved only in a secure and well-protected environment. To be compliant with SOX, identify the potential risks, and set security. Then, use ApexSQL Audit to audit and report SQL Server and database events
References:
1U.S. Securities and Exchange Commission A White Paper Proposing Practical, Cost Effective Compliance Strategies
September 25, 2013