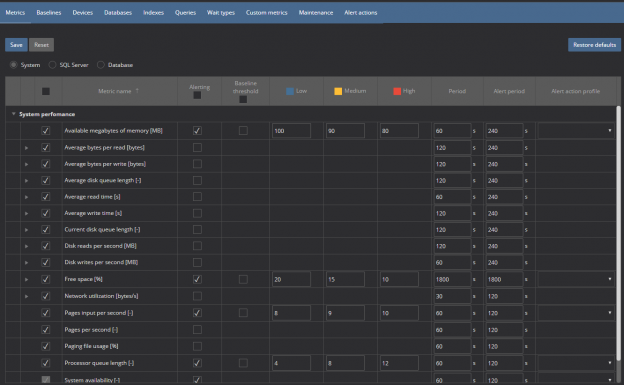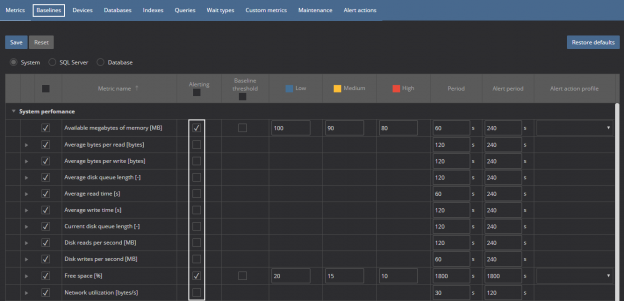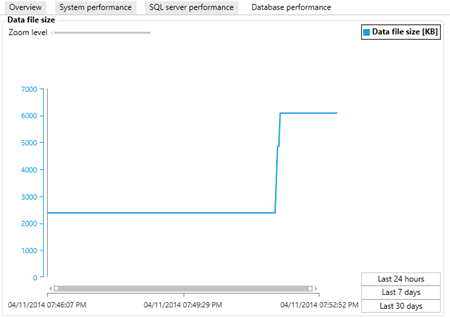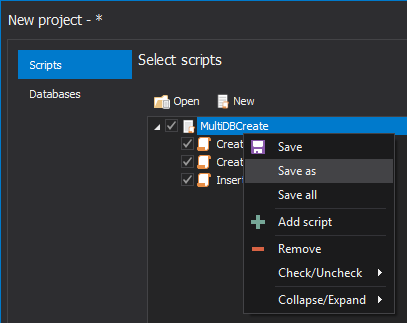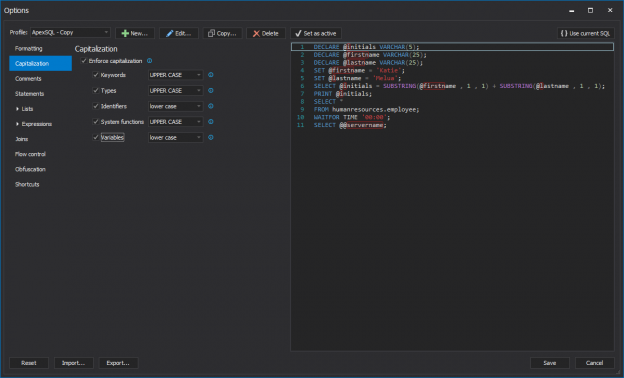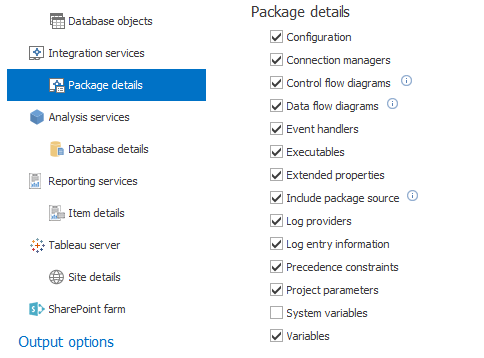
The data flow element is a part of a SSIS package that contains different type of data flow components:
- Source components – make data from different types of data sources available to a data flow
- Transformational components – aggregate, merge, distribute, and modify the data inside the data stream, and
- Destination components – load the data from the data flow into different types of data sources or create an in-memory dataset