What is SOX
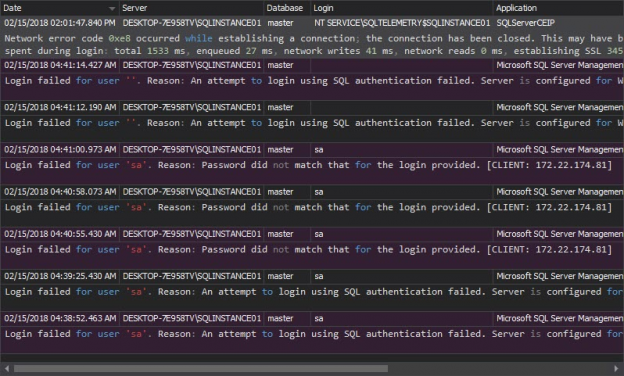
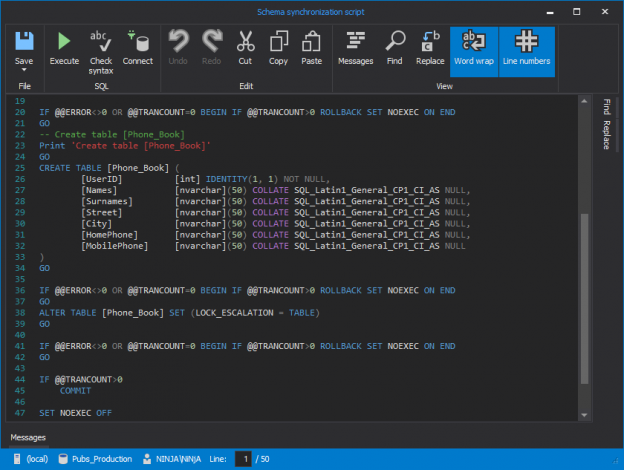
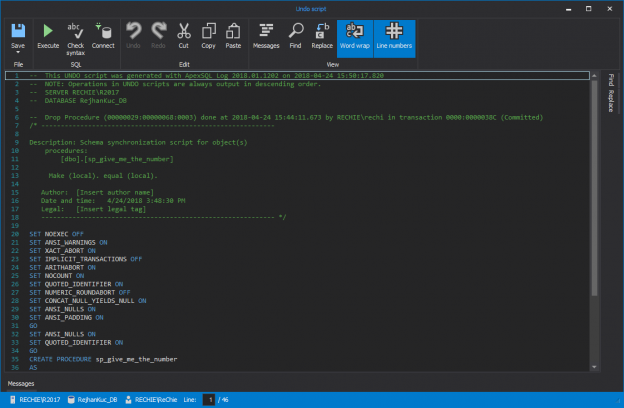
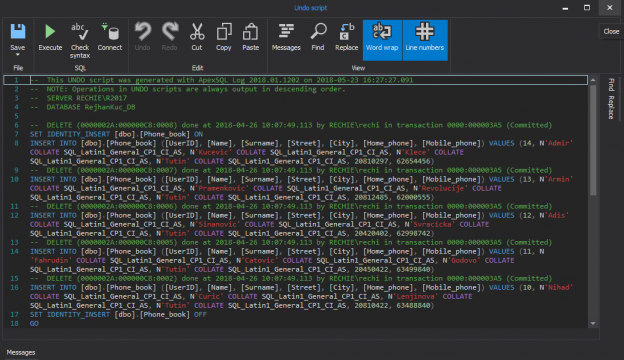
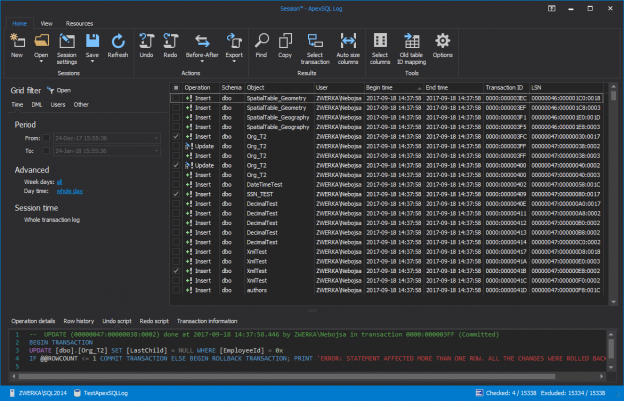
The Sarbanes–Oxley Act of 2002, Sarbanes–Oxley, Sarbox, or SOX is a regulation created to improve the quality and integrity of financial reporting. It addresses audits, financial reporting and disclosure, conflicts of interest, and corporate governance, so financial and business information is factual and accurate. Its purpose is to avoid accounting scandals like the ones in 1990s stock market.
September 25, 2013